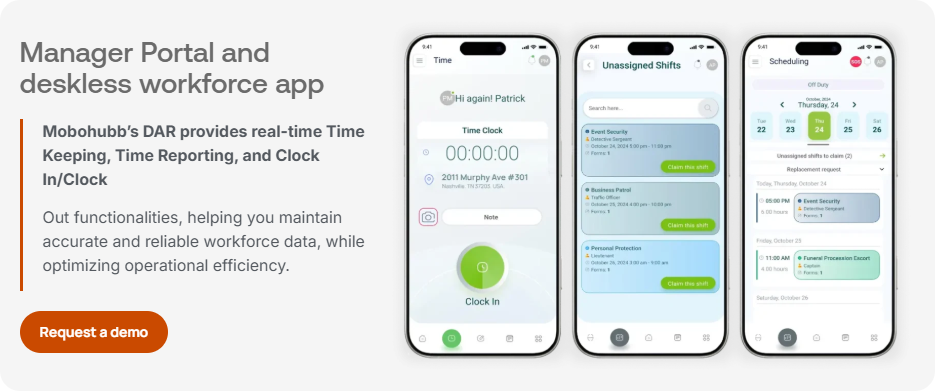
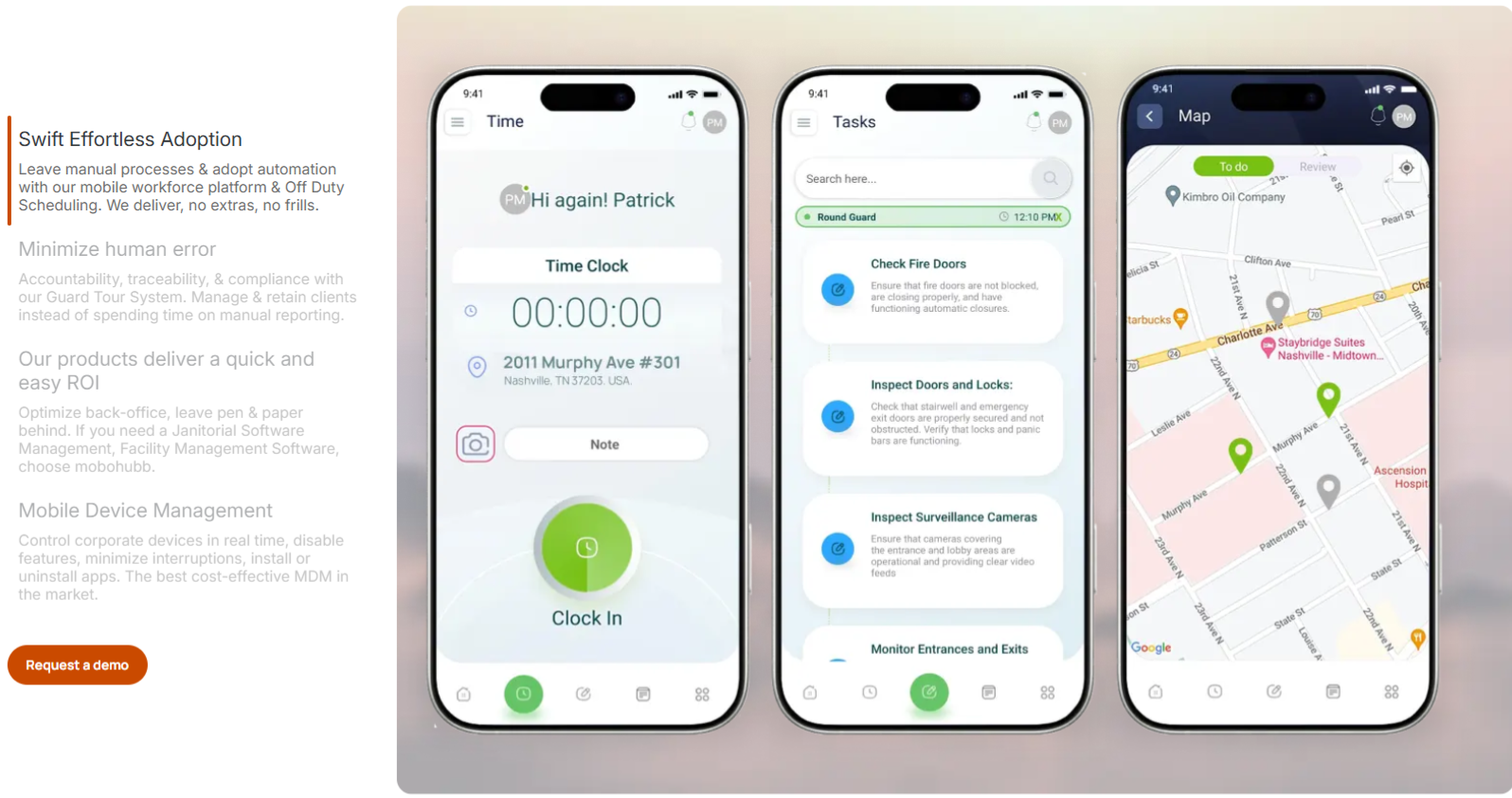
Mobile devices are crucial in optimizing workflows and enhancing cleaning, facility management, and security efficiency. Yet, this dependence also heightens the risk of security breaches. This article examines how Mobohubb’s cutting-edge solutions protect mobile devices while boosting productivity for teams without desks.
Importance Of Mobile Device Security
Mobile device security has become essential rather than optional in today’s interconnected workplace. Sectors like cleaning and facility management depend significantly on mobile tools for task management, progress tracking, and real-time communication. Securing these devices maintains seamless operations and protects sensitive business information from unauthorized access.
Common Security Threats To Mobile Devices
Understanding potential risks is the first step in securing your mobile workforce. Common threats include:
- Malware Attacks: Malicious software targeting sensitive data and disrupting operations.
- Phishing Scams: Fraudulent messages tricking employees into revealing confidential information.
- Device Theft: Physical loss of devices compromising sensitive business data.
- Weak Encryption: Inadequate protection for data stored or transmitted by devices.
Top Mobile Security Practices
To mitigate these risks, consider the following best practices:
- Implement Device Encryption: Protect sensitive data by encrypting devices, making it unreadable to unauthorized users.
- Install Mobile Antivirus Software: Regularly update antivirus tools to detect and neutralize potential threats.
- Enable Endpoint Security Measures: Monitor and manage devices remotely to address vulnerabilities proactively.
- Regular Security Training: Educate employees on recognizing and responding to security risks.
Choosing the Right Security Tools
Selecting the appropriate tools is critical to maintaining robust mobile device security. Mobohubb’s solutions include:
- Comprehensive Device Compliance Monitoring: Ensure all devices meet security standards.
- Cloud-Based Encryption Services: Protect data across all devices seamlessly.
- Real-Time Threat Detection: Identify and mitigate security threats instantly.
How to Implement Mobile Security Policies
A structured approach to policy implementation can significantly enhance your security framework. Key steps include:
- Assess Current Risks: Identify vulnerabilities in your mobile infrastructure.
- Define Security Standards: Set clear policies for device usage and data access.
- Enforce Compliance: Use tools like Mobohubb to monitor adherence to security protocols.
- Review and Update Policies: Continuously refine policies to address emerging threats.
Tips for Securing Employee Devices
Securing employee devices is crucial for industries relying on mobile workforces. Here are actionable tips:
- Mandate Strong Passwords: Require complex, regularly updated passwords for all devices.
- Enable Remote Wipe Capabilities: Protect data by remotely erasing it from lost or stolen devices.
- Use Multi-Factor Authentication: Add layers of security to access sensitive systems.
- Limit Third-Party App Usage: Restrict app downloads to pre-approved sources.
Checklist for Mobile Device Security Success
FAQs
- What is mobile device security? Mobile device security protects devices and their data from unauthorized access, ensuring safe and efficient operations.
- Why is it essential for industries like cleaning and facility management? These industries rely on mobile devices to manage tasks and communication. Securing these devices prevents data breaches and ensures uninterrupted workflows.
- How can Mobohubb enhance mobile security? Mobohubb offers tools like real-time threat detection, device compliance monitoring, and encryption services tailored for deskless teams.
- What are the key features of a firm mobile security policy? A robust policy includes encryption, multi-factor authentication, endpoint security, and regular employee training.
- How often should security policies be reviewed? Policies should be reviewed and updated annually or whenever new security threats emerge.
Related Content:







